When 74% of breaches trace back to human error or manipulation, tight manufacturing access control becomes non-negotiable. The sector’s current landscape is tricky, juggling rising security threats with the reality of high staff turnover. As evidenced by Epicor’s 2023 survey, 56% of the manufacturing employees they spoke to reported eyeing the exit in favor of greener pastures. This isn’t just about operational hiccups; it’s about the heightened risk of data breaches and unauthorized access every time someone packs up their desk.
Manufacturers are stepping up their security, deploying everything from fire alarms and intrusion detection to real-time video monitoring to protect their assets. Crucially, the push towards integrating secure remote access systems has become a game changer, ensuring factory machinery can be monitored and managed securely from anywhere, anytime.
Ready to tackle the beast of robust access control in manufacturing head-on? We’ll dive into understanding the role of manufacturing access control in facility security, tackle the challenges of sourcing temporary employees through third-party agencies, managing high staff turnover, and explore how to weave access control into the broader security fabric of the company. Read on to learn new strategies and security measures that safeguard your assets and also adapt to evolving threats and workforce dynamics.
Understanding access control in manufacturing facility security
Understanding access control in manufacturing facility security involves navigating a complex web of factors. The stakes are high: Inadequate controls can lead to significant risks, including unauthorized entry, whether intentional or not.
Considering the high employee turnover rate in manufacturing — whether from low salaries, no commitment from temporary workers, or even background checks being overlooked — the risk associated with managing access rights escalates. Each new hire or exit requires an update in access permissions, which, if not managed meticulously, can leave gaps in security. Imagine the challenge — it’s like having to change your house locks each time someone loses a key.
Manufacturing security is about physical barriers just as much as it’s about safeguarding digital realms. Your mission? Protect everything from the front gate to the file server. Think of it as not just locking your car but also having a system to prevent its computer system from being hacked. This requires a smart blend of physical and digital defenses to protect your assets comprehensively. Poorly managed access rights can also lead to theft or property damage, industrial espionage, and intellectual property theft, all of which can be devastating for any manufacturing business. It’s about more than just assets; it’s about protecting the lifeblood of your company.
Before giving that TED Talk on security best practices, you need a game plan. First, think regular check-ups – audit your manufacturing access controls like you’re diagnosing a patient, looking for any signs of weakness. Next, embrace the tech at your disposal. From biometrics to blockchain, the tools in your arsenal are evolving. Regularly review your access control protocols. Integrate the latest security tech that fits your operation. And most importantly, ensure your strategies are as dynamic as the threats you face.
Read more: Common IT Compliance Frameworks Supported by Resolver
Strategies for managing high turnover in manufacturing
In manufacturing, high employee turnover can significantly complicate access control management. Safeguarding access is more than an HR headache; it’s a security challenge. To effectively navigate this challenge, companies need to implement strategic solutions for managing access rights. Here’s how you can tighten the ship, ensuring both operational efficiency and secure access in your facilities:
- Automated access control systems: Let’s be honest, manual updates to access rights in a high-turnover environment are about as efficient as using a bucket to bail out a sinking ship. Modern manufacturing access control software solutions can automatically update access rights as employees come and go, drastically cutting down the risk of unauthorized entries or breaches.
- Rigorous credential management: With the turnover tide high, loose credential management could sink your security. Ensuring airtight procedures for activating and deactivating access rights is non-negotiable. Swift action in removing access for those who’ve departed, coupled with seamless onboarding for the newcomers, is your best defense.
- Temporary staffing best practices: Granting temporary staff the keys to the castle? Think again. Restricting access to only what’s necessary for their role and enforcing time restrictions for both temporary and permanent employees not only shields you from unnecessary exposure but also keeps your operations smooth and secure.
- Regular security audits: Conduct regular audits to identify any potential vulnerabilities in the manufacturing access control system, especially when dealing with a high turnover tide. More than mere checklists, this proactive practice ensures that any security gaps are identified and addressed promptly, ensuring you’re always battle-ready to plug any potential leaks.
- Training and awareness: Whether it’s your long-term first-mate or temporary deckhands, a well-informed team is your first line of defense. Enforcing mandatory training for all employees to educate the importance of security protocols turns your crew into a vigilant force, significantly lowering the risk of breaches.
- Tailored access rights: Customizing access rights based on employee roles and responsibilities minimizes risks without compromising operational integrity. Not every employee needs an all-access pass, and limiting access on a need-to-know basis can reduce the potential for security breaches.
Integrating manufacturing access control with other security
Integrating manufacturing access control with other security functions can help craft a more reliable and comprehensive security strategy. This integration, especially with Environmental, Health, and Safety (EHS) protocols, while gaining alignment from essential cross-functional teams and other critical stakeholders, including Facility Management, Human Resources, and Legal Teams, forms the backbone for a holistic security posture.
The goal? A seamless integration that not only addresses the flux of high employee turnover but also anchors the dynamic nature of the manufacturing workforce firmly within a secure framework.
- Understanding challenges and strategy design: Start by mapping out the specific hurdles manufacturing security faces, such as high turnover, diverse access needs, and meshing new systems with old ones. Your strategy should tackle these challenges head-on, championing connectivity and tech-forward solutions that keep pace with manufacturing evolution.
- Physical structure analysis: Evaluate the physical layout of your manufacturing facility. Which zones need a tighter grip? How does traffic flow through your space? Pinpoint where to deploy access controls for maximum impact without disrupting the day-to-day.
- Determining entrance control types: Select the appropriate types of access controls, such as biometric scanners, card readers, or keypads, based on the security needs of different areas. Assess the security level each area demands, the user-friendliness of the technology, and how well it plays with other systems. It’s about picking the right tool for the right job.
- System integration: The real magic happens when manufacturing access control actively communicates with other security systems like CCTV, alarms, and fire safety measures. This integration offers a panoramic view of your security landscape, enabling swift, coordinated action when things go south.
- Implementation and fine-tuning: Beyond installing and flipping the switch on your access control setup, focus on tailor-fitting the system to your unique security blueprint. Train your team to be proficient users, keep the system’s software sharp with regular updates, and stay ahead of both the curve of potential threats and the arc of tech advancements.
Embrace the future of security in manufacturing with Resolver
The pivotal role of advanced access control systems in the manufacturing sector is unmistakable. Beyond merely managing access, incident management systems form the cornerstone of an extensive security strategy, adept at tackling challenges from fluctuating employee numbers to safeguarding critical zones and intellectual assets.
Resolver’s Risk Intelligence platform facilitates the identification and prioritization of vulnerabilities, empowering facilities to strategize action plans with precision. Our tools not only boost efficiency and collaboration but also ensure regulatory compliance, aspects critical to any security strategy. With apps that allow you to go a step further by aggregating risk data and providing contextual analysis, we can help you reveal the true impact of risks on business operations.
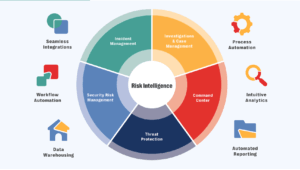
By integrating access control data with overall security management, Resolver’s Threat Protection Software offers a tailored approach to these challenges, through a unified security approach tailored to the specific needs of manufacturing facilities. Whether it’s navigating through the complexities of high staff turnover, fortifying entry points, or seamlessly blending access control with various security measures, Resolver’s solutions help you deliver all-encompassing protection to your organization.
Dive into the future of manufacturing security with Resolver. To experience the difference firsthand and discover how Resolver can revolutionize your approach to manufacturing security, book your custom demo now and take the first step towards a more secure, efficient, and future-proof manufacturing operation.
